Trustico® Online Security Blog
Say informed with the latest SSL Certificate news, security updates, and industry insights. Our articles cover everything from SSL Certificate management best practices to emerging cybersecurity trends and industry news.

Boost Rankings & Trust - The Importance of SSL ...
One key part of SEO is website security, especially using SSL Certificates. SSL Certificates protect users by encrypting data between their browser and the website. This security also affects SEO...
Boost Rankings & Trust - The Importance of SSL ...
One key part of SEO is website security, especially using SSL Certificates. SSL Certificates protect users by encrypting data between their browser and the website. This security also affects SEO...
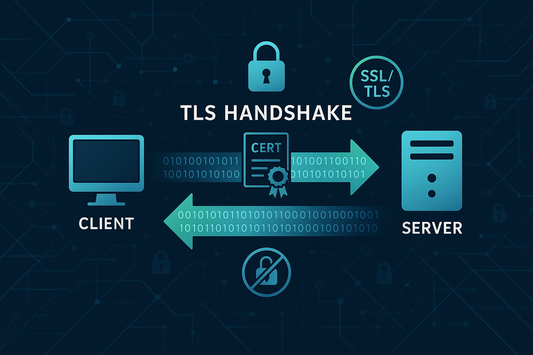
Understanding the SSL/TLS Handshake Process
The SSL/TLS handshake represents the initial negotiation phase between a client and server when establishing a secure connection. The SSL/TLS handshake consists of several distinct phases, each serving a specific...
Understanding the SSL/TLS Handshake Process
The SSL/TLS handshake represents the initial negotiation phase between a client and server when establishing a secure connection. The SSL/TLS handshake consists of several distinct phases, each serving a specific...

Certificate Authority (CA) Information
A Certificate Authority (CA) serves as a trusted third-party entity that issues, validates, and manages digital SSL Certificates that secure online communications and verify website identities.
Certificate Authority (CA) Information
A Certificate Authority (CA) serves as a trusted third-party entity that issues, validates, and manages digital SSL Certificates that secure online communications and verify website identities.
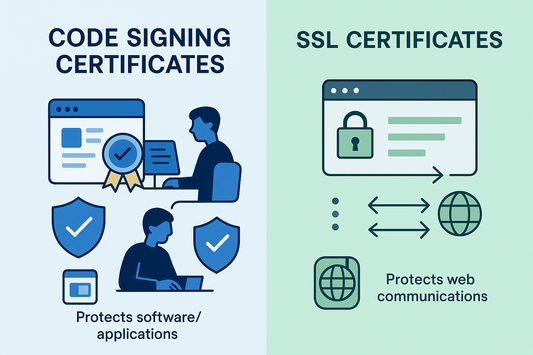
Code Signing vs SSL Certificates
While both utilize X.509 Public Key Infrastructure, they serve distinctly different purposes in the cybersecurity ecosystem. The confusion between these two types is understandable, as both require Certificate Authorities (CAs)...
Code Signing vs SSL Certificates
While both utilize X.509 Public Key Infrastructure, they serve distinctly different purposes in the cybersecurity ecosystem. The confusion between these two types is understandable, as both require Certificate Authorities (CAs)...

SSL Certificate Private Key and Public Key
Successfully deploying SSL Certificates requires understanding both the technical aspects of Private and Public Key cryptography and the practical considerations of web server configuration.
SSL Certificate Private Key and Public Key
Successfully deploying SSL Certificates requires understanding both the technical aspects of Private and Public Key cryptography and the practical considerations of web server configuration.

E-Mail Server Security and Encryption
Proper e-mail server security protects organizational reputation, ensures regulatory compliance, and maintains customer trust. Understanding how to implement SSL Certificates and other security measures is essential for protecting e-mail communications.
E-Mail Server Security and Encryption
Proper e-mail server security protects organizational reputation, ensures regulatory compliance, and maintains customer trust. Understanding how to implement SSL Certificates and other security measures is essential for protecting e-mail communications.
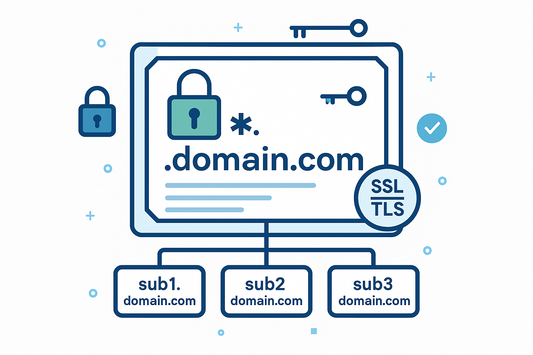
How to Generate the Certificate Signing Request...
Generating a Certificate Signing Request (CSR) for Wildcard SSL Certificates requires specific formatting that differs from standard SSL Certificates. The key difference lies in how you specify the domain name...
How to Generate the Certificate Signing Request...
Generating a Certificate Signing Request (CSR) for Wildcard SSL Certificates requires specific formatting that differs from standard SSL Certificates. The key difference lies in how you specify the domain name...
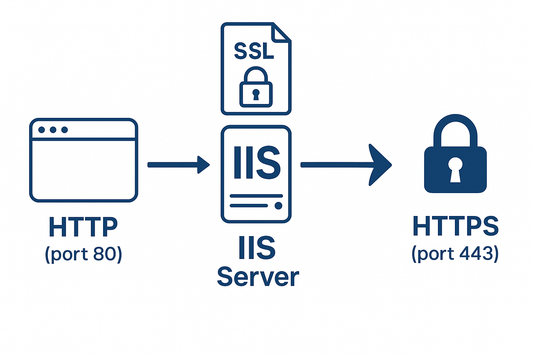
Redirecting HTTP to HTTPS in IIS Microsoft 7X a...
Without proper redirection, users may inadvertently access unsecured versions of your website, potentially exposing sensitive data and undermining the protection provided by your SSL Certificate investment.
Redirecting HTTP to HTTPS in IIS Microsoft 7X a...
Without proper redirection, users may inadvertently access unsecured versions of your website, potentially exposing sensitive data and undermining the protection provided by your SSL Certificate investment.
Stay Updated - Our RSS Feed
There's never a reason to miss a post! Subscribe to our Atom/RSS feed and get instant notifications when we publish new articles about SSL Certificates, security updates, and news. Use your favorite RSS reader or news aggregator.



